SSH
SSH mechanism
SSH (Secure SHell) is a network protocol and application generally used to access a shell account on a remote machine.
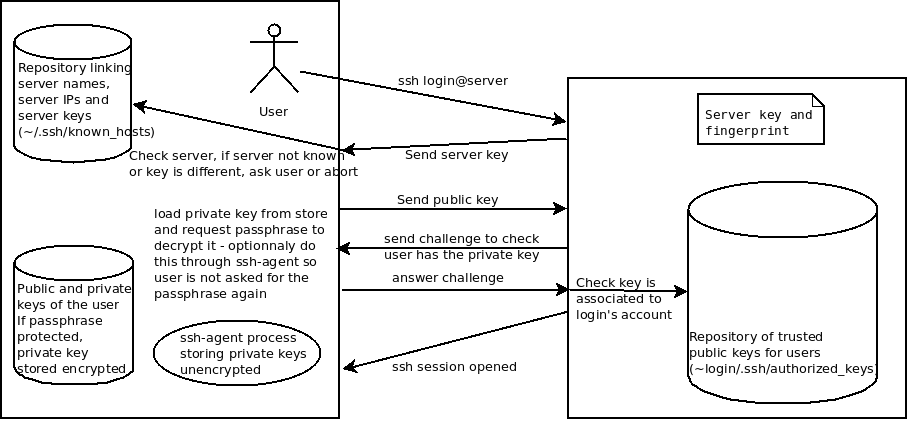
Establishing secure connections involve a few steps that are (badly) summarized in the following schema and commented below:
- In the first step, you instruct a client program (here
sshto connect to a givenserveras userlogin). You need to use the login given to you when registering as a Grid'5000 user when connecting to Grid'5000. This step triggers the next steps. - In the second step, the ssh client will attempt (default behavior) to check that the server answering the request is really the server you asked for. If it has never connected to that server, it will (by default) ask you to confirm that the certificate presented by the server is the one you expect by presenting is fingerprint. If you confirm, it will store the server, the IP of the server and the fingerprint in an internal database. Should the server certificate change (because traffic is highjacked, or because the server was changed without taking care of keeping its certificate), your ssh client will warn you something suspect is happening. You will need to investigate and either update the internal database (in general, the known_hosts file) or decide to abort the connection attempt until you are certain nothing suspicious is happening.
- Once the server is authenticated, you will need to prove you are user
login. This is done repeatedly (servers are by default configured to abort after 5 attempts) by:- sending (one of) your public keys. Unless you have explicitly (option -i for openssh) specified the key to use, the ssh client will look for reasonable keys to present to the server. In general, key stored in ~/.ssh and named id_rsa is chosen first, then the others in the directory.
- The server will answer by sending a challenge to check you own the private part of the key.
- The client will attempt to answer the challenge by either:
- requesting the passphrase to decrypt the private key directly.
- delegating the task of answering to the challenge to a agent provided by the OS (in general
ssh-agent). This agent might have loaded and deciphered the private key when you opened a session on your work machine, or might in turn request the passphrase. In general, agents keep all the information needed to answer other challenges for the key until they are restarted. They might store that information securely using OS mechanisms so it is available even after the next reboot.
- If the challenge is met successfully, proving you are a legitimate owner of the key-pair, then it will check if user login is allowed access with that key-pair by checking if the public key is associated to the login account. List of authorized_keys for user
loginis in general stored in~login/.ssh/authorized_keys. Management of this file by the user himself is not always possible directly. This depends on the security policy for the server.
- Finally, if the user is authenticated, the ssh session is opened. The ssh session might open a shell, perform commands, give access sftp for file management, copy files, etc…
Keys generation
- You (the user) generate a key pair using
ssh-keygen. The public key can then be used to encrypt messages that only the private key will be able to decrypt.
Generating public/private rsa key pair. Enter file in which to save the key (/home/login/.ssh/id_rsa):(press Enter)Enter passphrase (empty for no passphrase):(enter passphrase and press Enter)Enter same passphrase again:(enter same passphrase and press Enter)Your identification has been saved in/home/login/.ssh/id_rsa.Your public key has been saved in/home/login/.ssh/id_rsa.pub.
- Upload the public key (
/home/login/.ssh/id_rsa.pub) using the Account Management Interface. The key is copied to the list of keys used to authenticate you (~/.ssh/authorized_keys). - When you try to connect to Grid'5000, the Grid'5000 SSH server encrypts a message (the challenge) using your public key, and sends that encrypted message. If your SSH client can decrypt the message, and send it back to the server, the server will have verified your identity. That step is performed automatically when you try to connect. Additionally, if you use an SSH agent, you can avoid typing the key's passphrase at each connection.
SSH-based tools such as scp and rsync can also be used to transfer files to/from Grid'5000.
Basic usage
Connection to a machine
or
see man ssh for options
Copying files
Grid'5000 users have home directories in every Grid'5000 sites. But each site home directory is accessible in the access machines in a directory named after the site name.
To copy myfile from my workstation to my nancy home:
To copy myremotefile from my lyon home to my workstation:
To copy mydir from my workstation to my nancy home:
Mounting remote filesystem
To mount a remote filesystem using sshfs:
To unmount the remote filesystem :
Complex usage
Copying mydir to my rennes home with rsync or tar:
rsync
To synchronize through SSH:
tar/ssh
To preserve things:
SSH keys handling
SSH key types
SSH support 3 types of keys:
- rsa1: RSA algorithm, SSH protocol version 1 (default key name: identity), DEPRECATED
- rsa: RSA algorithm, SSH protocol version 2 (default key name: id_rsa)
- dsa: DSA algorithm, SSH protocol version 2 (default key name: id_dsa), DEPRECATED since OpenSSH 7
You are advised to use a rsa key.
SSH key passphrase
An SSH key-pair is a set of 2 files. A rsa key-pair for instance is:
- id_rsa: the private key, to be kept on a safe storage, no permissions on the file for anybody except you (i.e. mode 600).
- id_rsa.pub: the public key, to be dispatched on the systems that you want to connect using SSH (within the authorized_keys files)
The general case
In order to protect your private key from being maliciously used to access your systems (if one steals your private key file for instance), you must provide a passphrase. Empty passphrase should only be used for SSH host key generation (normal users should not have to care about this), or for system accounts keys that need automatic (none-interactive) login on remote systems (no passphrase eases scripting ;) ).
For user's usage, you actually wont have to enter your passphrase each time you access to a system using SSH, since you can use a ssh-agent. This agent store it for you indeed, so that you only need to enter your passphrase one - and only one - time.
The Grid'5000 case
It is common usage on HPC cluster to use SSH keys without passphrase, so that connection to nodes can be scripted, and never interrupted by any authentication interactive process. Furthermore, using a ssh-agent is often not a good solution, because it doesn't work well with shell scripts, non-interactive sessions, screen sessions ... because you are always asked to enter your passphrase once.
The advice then is to use a SSH key with passphrase to access the frontal of the cluster, and then store on your Grid'5000 home directories a dedicated key without passphrase.
SSH Key generation
Please use the command "ssh-keygen -t rsa" to generate your SSH RSA key, and give a non-empty passphrase.
- You (the user) generate a key pair using
ssh-keygen -t rsa. The public key can then be used to encrypt messages that only the private key will be able to decrypt.
$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/bob/.ssh/id_rsa): Enter passphrase (empty for no passphrase): ******************** Enter same passphrase again: ******************** Your identification has been saved in /home/bob/.ssh/id_rsa. Your public key has been saved in /home/bob/.ssh/id_rsa.pub. The key fingerprint is: 00:11:22:33:44:55:66:77:88:99:aa:bb:cc:dd:ee:ff bob@leponge
SSH Key usage
Once you generated your key, you need to dispatch its public part on every server you may want to access. This means adding the content of the id_rsa.pub file into the remote .ssh/authorized_keys file of every server. For Grid'5000, you need to understand that you have a different home directory for each site, and therefore that for each site you plan to access, you need to dispatch your public key on your home directory on that site. To dispatch your id_rsa.pub public key on the server named myserver (login mylogin), you may use the following command:
$ MYSERVER=myuser@myserver $ cat ~/.ssh/id_rsa.pub | ssh $MYSERVER 'umask 022 ; mkdir -p .ssh ; touch .ssh/authorized_keys ; cat >> .ssh/authorized_keys'
A command named ssh-copy-id may be provided within the SSH package installed on your system. In such a case, you may simply run:
$ ssh-copy-id myuser@myserver
NB: this requires your key(s) to be stored in a SSH agent, see below.
Using the SSH agent
- Storing keys and passphrases
To tell the ssh-agent to store your key AND remember the passphrase so that you do not have to enter it everytime you connect via SSH to a remote machine, just do a:
$ ssh-add Enter passphrase for /home/bob/.ssh/id_rsa: ******************** Identity added: /home/bob/.ssh/id_rsa (/home/bob/.ssh/id_rsa)
You may look at the keys the agent actually stores with the following command:
$ ssh-add -l 2048 SHA256:Bx7zKapa1Gz04+LtvxTsQCkvojKjB2iPmx2OLxfkXjl /home/bob/.ssh/id_rsa (RSA)
- forwarding the agent (useful if chaining SSH connections)
If not activated by default, you may need to run the SSH command with the `-A` parameter in order your key storage agent to be forwarded on connected hosts, so that you can chain other SSH command from this host without password or passphrase afterward. (try a `ssh-add -l` on the remote host to check if your key is forwarded). You may also add a "ForwardAgent yes" statement in your .ssh/config file.
Be warned that forwarding the agent (and then the data it stores) on a unsecure remote server may be unsafe.
Setting up a user config file
Setting up aliases or defaults
You may provide a configuration file that define default parameters for your SSH connections inside Grid'5000. This file is ~/.ssh/config in your Grid'5000 account home directories (one per site). In this configuration file, you may for instance specify:
- alias for long hostnames
- username to be used to connect some machines if this is not the one used localy (no more need for either "-l username" or "username@" statement).
- X11 forwarding enabling
- TCP port forwarding
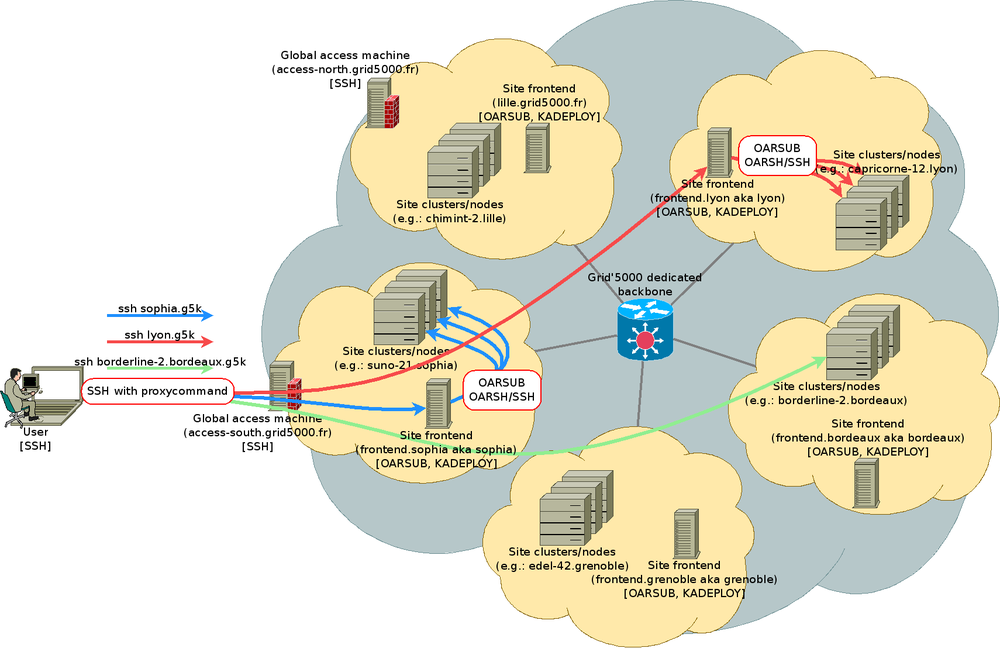
Using SSH with ssh proxycommand setup to access hosts inside Grid'5000
You can setup your local (on your laptop or workstation) .ssh/config so that you transparently access any host inside Grid'5000 (behind Grid'5000 firewalls). The idea is that your local ssh client will directly talk with the ssh daemon on the host behind the firewall through a connection to the gateway opened with another ssh connection.
First: setup an alias for the global access machine
# Alias for the gateway (not really needed, but convenient)
Host g5k
User g5k_login
Hostname access.grid5000.fr
ForwardAgent no
Your are now able to connect to your Grid'5000 site without being bothered with options such as to specify your Grid'5000 login each time:
ssh g5k scpmy_directory/my_fileg5k:site/
Second: setup the glob alias for the access to any hosts inside Grid'5000
(host inside Grid'5000, except the access machine are not reachable from the Internet)
# Automatic connection to hosts within Grid'5000, and not reachable direction on SSH tcp port 22
Host *.g5k
User g5k_login
ProxyCommand ssh g5k -W "`basename %h .g5k`:%p"
ForwardAgent no
The .g5k suffix is an arbitrary suffix you will now specify in your command lines in order to access hosts inside Grid'5000: And now, to log on that gateway, you can use:
- Accessing the frontend of my site (grenoble)
ssh grenoble.g5k
- Accessing the frontend of another site
ssh rennes.g5k
- Accessing a node belonging to one of my job
ssh graphite-3.nancy.g5k
- Copying files
Any command (scp, rsync, ...) can use the .g5k magic suffix.
scp myfile rennes.g5k: rsync -avz mydir rennes.g5k:
Global picture
Using SSH with ProxyJump to access hosts inside Grid'5000
Basics
ProxyJump was introduced in ssh version 7.3 to made it easier to do the jump and internal login in one step.
Here is the basic syntax with the -J flag:
ssh -J <access-host> <remote-host>
And a Grid'5000 example to connect to Nancy's frontend:
ssh -J access.grid5000.fr fnancy.nancy.grid5000.fr
Single remote host aliases
Like ProxyCommand, ProxyJump can be used in your local .ssh/config.
However, ProxyJump can't use `%h` or `%p` ssh variables nor `basename` command. So a general/wildcard suffix can't be used like previous ProxyCommand configuration to access to any hosts inside Grid'5000.
But you can easily use some single host alias configuration like this Nancy's frontend example:
Host myfrontend
User g5k_login
HostName fnancy.nancy
ProxyJump access.grid5000.fr
ForwardAgent no
and so directly connect with:
ssh myfrontend
Tips
bash-completion
The bash-completion package eases the ssh command usage by providing completion for hostnames and more.
yum install bash-completion
On Debian:
apt-get install bash-completion
Using port forwarding
A SSH connection allow you to tunnelize other connections. This is achieved using the "-L", "-R" parameters.
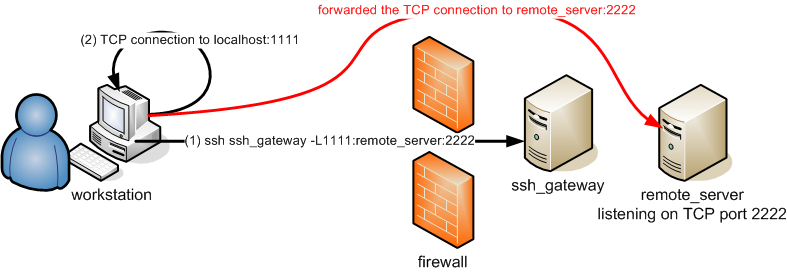
Forwarding a local port
You can forward a localport to a host behind a firewall.
In this case, the target remote server must be explicitly given in the ssh command.
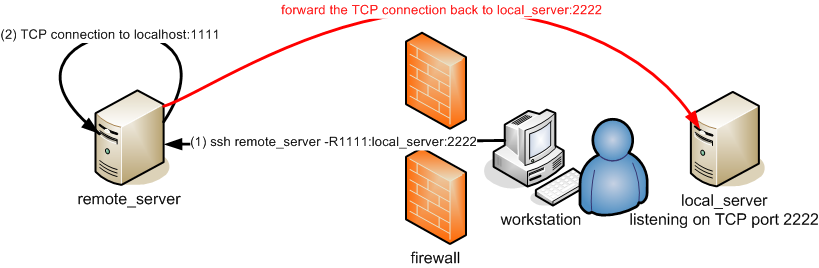
Forwarding a remote port
You can forward a remote port back to a host protected by your firewall.
In this case, the target local server must be explicitly given in the ssh command.
Tunnelizing for others
Using the "-g" parameter, you allow connections from other hosts than localhost to use your SSH tunnels. Be warned that anybody within your network may access the tunneled host this way, which may be a security issue.
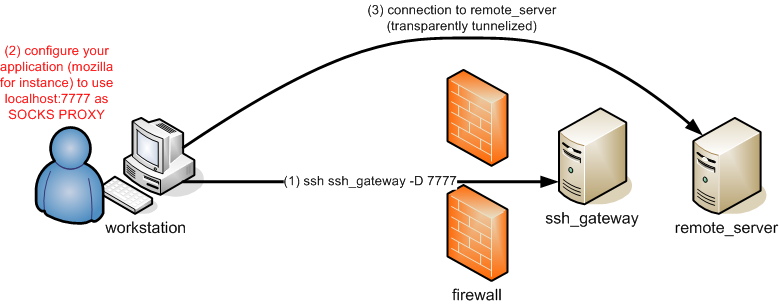
Using OpenSSH SOCKS proxy
OpenSSH ssh client also embeds a SOCKS proxy. You may activate it using the "-D " parameter and then configuring your application (Mozilla Firefox for instance) to be proxified through the so created SOCKS proxy.
It is also possible to configure your web browser to use a different proxy depending on the destination to reach. This can be achieved using Foxyproxy (a browser extension) (or using a proxy autoconfiguration script).
In this case, no target remote server needs to be given in the ssh command line. The socks client (e.g. Firefox) can talk to target address.
| Note | |
|---|---|
If using SSH tunneling does not suit your needs, for instance because your client application does not support the socks protocol, or because you do not manage to get things working as you like, mind looking at Grid'5000 VPN, which provides another way to reach services in Grid'5000 from the outside. | |
Escape characters
- ~.
Disconnect you, even if your remote command hangs.
- ~C
Open command line. Allows the addition of port forwardings using the -L and -R options.
See `man ssh' for more details
SSH resources
Un*x clients
- OpenSSH
OpenSSH is available in every good linux distro, and every *BSD, and Mac OS X.
Mac OS X tools
- SSHKeychain is a Cocoa application that acts as a frontend to
ssh-agent. It uses the Mac OS X Keychain to store the key (so you don't have to remember another password), and it can manage a set of tunnels. - Cyberduck is a Cocoa FTP and SFTP client.
Windows clients
- OpenSSH is natively available since Windows 10 April 2018 Update.
- OpenSSH/Cygwin
OpenSSH is available with Cygwin. You may then find the same features in your SSH client even if you run Windows. Furthermore, Cygwin also embeds many other GNU Un*x like tools, and even a FREE X server for windows. USE CYGWIN ;). URL: http://www.cygwin.com/
- Putty
Free windowish SSH client: http://www.chiark.greenend.org.uk/~sgtatham/putty/
- www.ssh.com client
Free for non commercial use windows client: http://www.ssh.com/support/downloads/secureshellwks/non-commercial.html
Automatic proxy configuration file
| Note | |
|---|---|
This is an alternative to Foxyproxy. | |
In order to use a different proxy depending to the target to reach, You may create the following PAC script on your workstation (e.g. in /home/bob/ssh-socks.pac) and set it in firefox's proxy configuration settings (e.g. file:///home/bob/ssh-socks.pac). In the script, fill the urls array object with target urls as you need.
//+---------------------------------------------------- //| Hosts to proxify are set in the urls array. //| This script assumes that the proxy to reach those //| hosts is listening on localhost:7777, e.g. created //| with `ssh -D 7777 access.grenoble.grid5000.fr' //+---------------------------------------------------- var urls = new Array( "http://edel-42.grenoble.grid5000.fr*", "https://adonis-3.grenoble.grid5000.fr*" ); function isProxified( url ) { for (var i = 0; i < urls.length; i++) { if( shExpMatch(url, urls[i] ) ) return 1; } return 0; } function FindProxyForURL(url, host) { if (isProxified(url)) return "SOCKS localhost:7777"; else return "DIRECT"; }